Latest Articles
Azure Storage Basics and How It Works
Azure Storage is a cloud service from Microsoft that stores your data safely and within easy access. It is highly depend...
Top Tableau Q and A for Freshers and Experts in 2025
In this Tableau interview questions and answers blog, I have put together the most usual interview questions. The questi...
Blockchain Categories and Why They Matter
Blockchain became well-known due to Bitcoin, and it changed the way people perceive online transactions. When people sta...
AWS Basics What is Amazon Web Services
Netflix did not select AWS at random. They did so because AWS provided them with greater flexibility and numerous useful...
Scrum DevOps and the Future of Development in 2025
In 2025, the optimal way to write software varies based on what one organization requires. Scrum is excellent for team c...
Skills for Program Managers to Guide Teams Successfully
A program manager is an individual tasked with a collection of related projects, a program, to complete on time and to s...
Basics of Quality Control You Should Know
Nowadays, we generally expect products and services to function without giving much thought to it. However, in the early...
The Role of Ethical Hacking in Securing Data
Hacking is illegally using another person's computer system. A hacker is a person who prefers to know about computer...
5 Breakthrough Trends in Modern Content Marketing
Your content is the basis of all your online marketing. It can break your campaign or make it. Content ties your brand t...
Power BI Interview Q and A Guide for 2025
Power BI is a common tool for data analysis and creating visual reports. It assists individuals in transforming intricat...
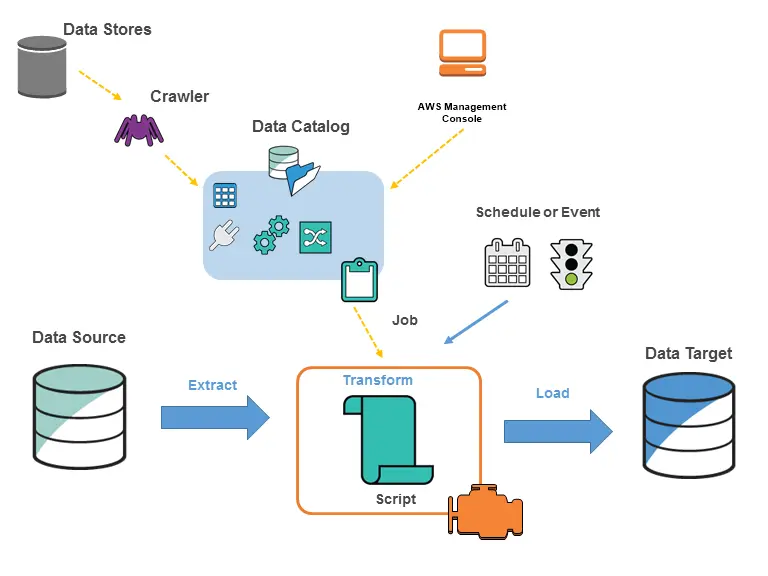
ETL Optimization Using AWS Glue Services
AWS Glue is a tool that assists you in migrating and organizing data in an easy and quick manner. It is a managed ETL se...
Understanding Blockchain Made Easy for Beginners
There is so much buzz about "blockchain" and "cryptocurrencies" in the tech community and even in th...


.jpg)



.png)
.webp)

.webp)




.webp)