Articles on Other
Transforming Customer Satisfaction into Customer Delight
Customer Satisfaction comes with top quality and on-time delivery as captured/defined in the Scope. Customer Delight is ...
Explore RTI: Insights, updates, and resources in one blog
“We hold these truths to be self-evident that all men are created equal” – and equality is evident at ...
When the Stakes Are High: Master Stakeholder Management.
Reputation management is critical to business interest. Customer experience is THE differentiator in moving the needles....
Certification Matters: Why You Should Choose iCert Global?
image courtesy:https://www.roberthalf.com/sites/default/files/styles/blog_image/public/Media_Root/images/blog-fa/11-2_ce...
iCert Global Awarded the Arch of Excellence by AIAC 2016
iCert Global , the Startup from Houston, that stood top wining the ARCH of Excellence 2016 Award from AIAC Excellence 20...
iCert Global CEO: The Standard Is to Always Outperform!
There was something more assertive in the tone of the young entrepreneur who still in his twenties has nearly 8 years of...
How iCert Global empowers the Professionals across the Globe
iCert Global is the fastest growing Education Industry, both as an Accredited Training Organization (ATO) and Accredited...
Understanding the True Cost of Employee Engagement in HR
(an account by one of our staff) Personal stories really connect. One of the employees seeking a day off met the HR for ...
Earn as You Learn: Secure Your Professional Certification
Haven’t we read that before? Yes, but it never hurts to read once again. How many times you would have watched the...
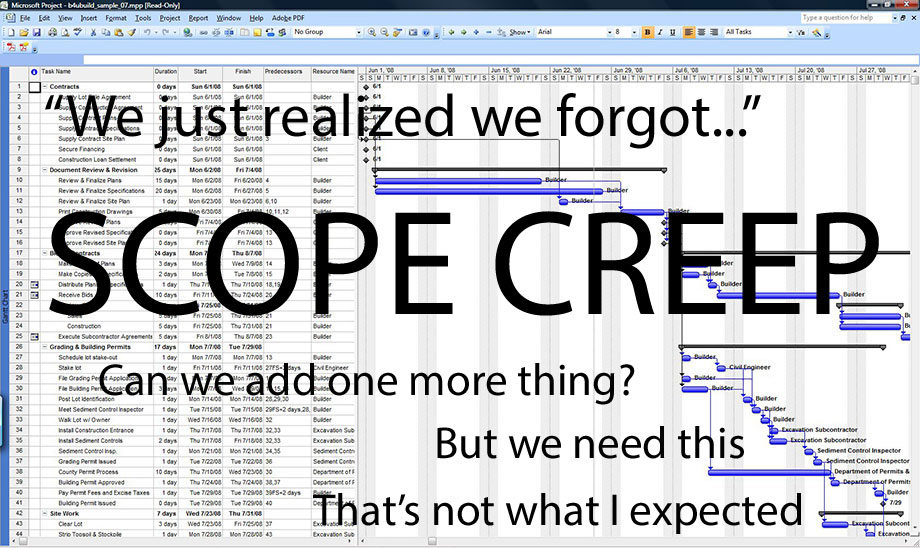
Scope Creep: A Slippery Slope to Achieving Project Success
(A personal account of the perils of scope creep) As Jobs puts it ‘we can only connect the dots afterwards’....
Managing People as Valuable Asset for Organizational Success
‘When dealing with people remember you are not dealing with creatures of logic but creatures of emotions – D...
Who Are Your Stakeholders?Understand and Manage Effectively
Ah! That’s an interesting poser and a twisted one too. I was engrossed in a status update with a developer, and lo...



.jpg)