Latest Articles
Why Digital Marketing Matters for Business Growth Today
Every company wants to attract as many customers as possible. Marketing gets people inside, and turns them into buyers. ...
Ansible versus Chef DevOps Tool Key Difference Explained
If you are working in DevOps, which is a method for creating and managing software, you may know there are many tools av...
Essential Role and Duties of a Scrum Master Explained Well
Agile approaches are increasingly finding their way into many organizations. An agile way of working, like Scrum, helps ...
Understanding Software Project Management Basics
Software project management is the act of planning and directing software projects. It is a special form of project mana...
10 Reasons AWS Skills Are in High Demand
We are an Education Technology company providing certification training courses to accelerate careers of ...
How Blockchain is Redefining Business and Society
Blockchain is technology that leads people to trust each other. Blockchain has the potential to change the manner in whi...
Creating Lessons Learned in Project Management
When a project is complete, it is time to celebrate, right? Not so fast - you are not truly finished until you hav...
Key Reasons to Take Cyber Security Seriously
Over the past few years, jobs in Cybersecurity have experienced rapid growth. More and more people are choosing Cybersec...
Breaking Down Big Data Issues,Insights and Case Study
Before we address the problems of Big Data, let us know what Big Data is. "Data" is any information that a com...
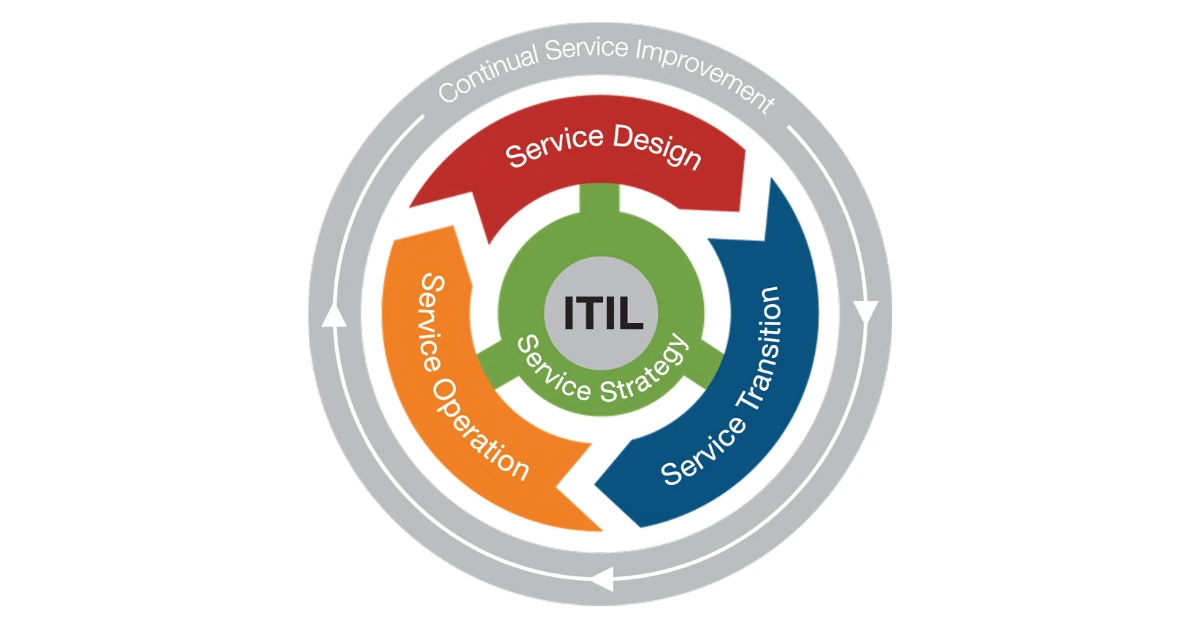
5 Vital Functions of ITIL Service Strategy
ITIL means Information Technology Infrastructure Library. It is a set of simple rules that help software and IT workers ...
5 Actionable Scrum Tips to Improve Your Team
Using Scrum can help your team create and launch a great digital product, but just saying "Scrum" won’t ...
Traditional Versus Digital Marketing Key Differences Guide
There are many ways a company can get people’s attention. One important way is through marketing, which helps busi...


.jpg)









.webp)