Latest Articles
Blockchain in Quality Management: Revolutionizing Data Security and Traceability
In an era of data, an unexpected number illuminates the crucial gap: a study commissioned in 2024 discovered that busine...
How Cybersecurity Impacts Quality Management in the Digital Era
In today’s digital-first landscape, effective cybersecurity strategies are directly tied to quality management, en...
How AI and Machine Learning Are Transforming Project Management
An unexpected trend is redefining the project management field. As project success rates have routinely been below 50%, ...
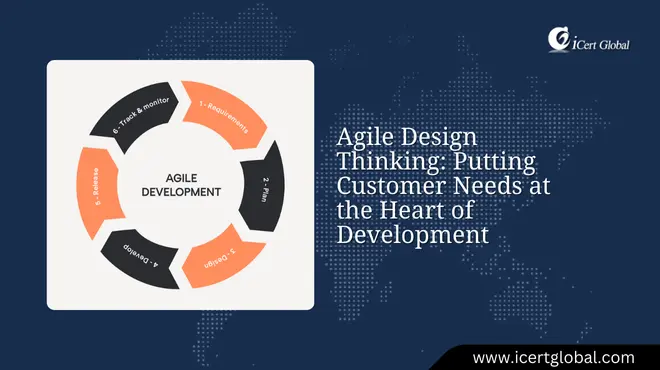
Agile Design Thinking: Putting Customer Needs at the Heart of Development
Agile Design Thinking is shaping the future of product development in 2025 by keeping customer needs at the center while...
Real-Time Business Analytics: Driving Faster Decision-Making in Enterprises
Business Analysts are no longer just requirement gatherers—they are strategic partners, using real-time business a...
Why Computer Security Should Be Your 1st Priority This Year
Future-facing cybersecurity challenges make it clear that strengthening your computer security today is key to preventin...
Data Literacy in the Digital Age: How Minitab Makes Statistics Accessible
Fewer than 12% of employees globally are very confident in their data skills, yet 85% of business executives believe suc...
Advanced Statistical Techniques in Minitab: Tips for Data Scientists
Forrester recently conducted a study in which they discovered that businesses utilizing advanced analytics and statistic...
Content Marketing in 2025: From Creation to Conversion
From creating compelling content to converting leads, content marketing in 2025 works hand-in-hand with social media str...
Exploring Deep Learning for Natural Language Processing in 2025
Stanford's recent AI Index study discovered that scores on challenging AI examinations rose as high as 67.3 percenta...
The Growing Importance of CCNP in Cybersecurity careers in 2025
According to recent industry analysis, a staggering 75% of networking professionals report that the fields of cybersecur...
How Agile Design Thinking is Shaping Product Development in 2025
In 2025, Agile combined with design thinking is helping organizations rethink traditional product development approaches...



.jpg)






.webp)